Inno Setup has long supported code signing (since v5.2.4). Fortunately, the way the authors of Inno Setup implemented this feature makes it really easy to use custom tools to do the code signing. In this post we'll take a look at how to use Signotaur with Inno Setup.
There are a few different ways to specify which command to run during signing with Inno Setup.
Sign Tool settings in Inno Setup IDE
The first is to define "Sign Tool" commands in the Inno Setup IDE. You can create multiple commands - for example if you have multiple certificates - and then in your scripts you can point to the "Sign Tool" you want your setup script to use.
To define a "Sign Tool" command in the IDE - tools menu, Configure Sign Tools...
The name can be anything you want, however if you are including other third party inno scripts you should make sure the name is unique to make sure those scripts cannot redefine the command (this is pointed out in the docs)
Imagine if a third party script did this
[Setup]
SignTool=Default cmd /c format.com z: $f
If a Sign Tool named Default is defined in the inno IDE, that would be used. Of course you should always review any third party code before using it!
After providing a name, you are prompted for a command. This is where we can provide our Signotaur command line.
Inno Setup will replace a few placeholders
$f, replaced by the quoted file name of the file to be signed. (required)
$p, replaced by the Sign Tool parameters (more on this later).
$q, replaced by a quote, useful for defining a Sign Tool which contains quotes from the command line.
$$, replaced by a single $ character.
So with that, lets build our command line (adjust to suite your scenario).
e:\SignotaurClient\SignotaurTool.exe sign --sign-server https://mysignotaurhost:91/ --api-key *** --thumbprint YOURCERT-THUMBPRINT --fd "SHA256" --description "My Application" --tr http://timestamp.sectigo.com --td "SHA256" --allow-untrusted $f
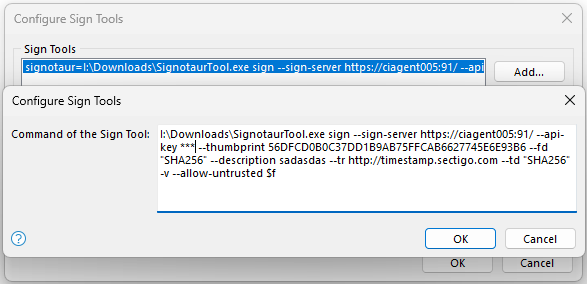
Note - in Inno Setup 6.3.3 and earlier, the Sign Tool command line limit is 256 chars, which is a problem when using signotaur - this was fixed in 6.4.0. The work around for 6.3.3 or earlier is to modify the registry - under HKEY_CURRENT_USER\Software\Jordan Russell\Inno Setup\SignTools find the value for the Sign Tool you added and enter the full command line there.
Make sure to restart the Inno Setup IDE after making the registry change.
Now we can define which Sign Tool to use in our Innosetup project.
[Setup]
SignTool=signotaur
That's all we need for now - you should be able to see Signotaur being invoked to sign the uninstaller and the installer.
One downside to this configuration is that there is no way to parameterize the Sign Tool command, so no way to avoid hard coding the ApiKey in the command (which is stored insecurely in the registry). For that reason alone, I do not recommend configuring the Sign Tool this way.
Sign Tool settings in the setup project
So lets look at the second option, which is to fully define the SignTool command in the [Setup] section. IMPORTANT : Firstly, to keep the IDE happy, define your signtool as above, but with a command of
$p
then in your innotsetup project :
[Setup]
SignTool=signotaur e:\SignotaurClient\SignotaurTool.exe sign --sign-server https://mysignotaurhost:91/ --api-key **** --thumbprint YOURCERT-THUMBPRINT --fd "SHA256" --description "My Application" --tr http://timestamp.sectigo.com --td "SHA256" --allow-untrusted $f
Note that Signtool name in the project must be one that is defined in the IDE
That works fine, but of course now instead of hard coding the ApiKey in the registry, we have it in our project file - which is potentially worse since it's likely checked into version control (perhaps even in a public repo on GitHub!).
Sign Tool settings on the command line
To get around this, we need to change how we compile our Inno Setup projects. Using the Inno command line compiler lets us get around all of the issues.
To do this, remove the Sign Tool configurations from the IDE - we won't be using them.
In our project, we can use the pre-processor to only run the SignTool when Release is defined.
[Setup]
#ifdef Release
SignTool=signotaur SignotaurTool.exe sign --sign-server {#signotaurServer} --api-key {#apiKey} --thumbprint {#thumbprint} --fd "SHA256" --description {#MyAppName} --tr {#timeStampServer} --td "SHA256" -v --allow-untrusted $f
#endif
On the command line we can can provide values for the pre-processor defines
/DRelease /DapiKey=abcdef ...
That now moves the ApiKey to your build script.
There is one last option we can explore here - that is to provide the entire Sign Tool command on the command line for the iscc compiler
/Sname=command
Sets a SignTool with the specified name and command
e.g.
/Ssignotaur e:\SignotaurClient\SignotaurTool.exe sign --sign-server https://mysignotaurhost:91/ --api-key **** --thumbprint YOURCERT-THUMBPRINT --fd "SHA256" --description "My Application" --tr http://timestamp.sectigo.com --td "SHA256" --allow-untrusted $f
This is what the FinalBuilder InnoSetup action uses when you use the SignTool property. Of course you can use FinalBuilder variables for the ApiKey and other parts that might change. If you are calling FinalBuilder from a CI server, those variables can be provided from the CI tool - so the secret is stored and secured in one place.
One last comment before I wrap this up - why would I need Innosetup to handle Code Signing, can't I just sign the resulting setup.exe myself? The main reason for letting Innosetup handle code signing the installer is that it also signs the uninstaller.